What Is Sharding?
What Is Sharding?
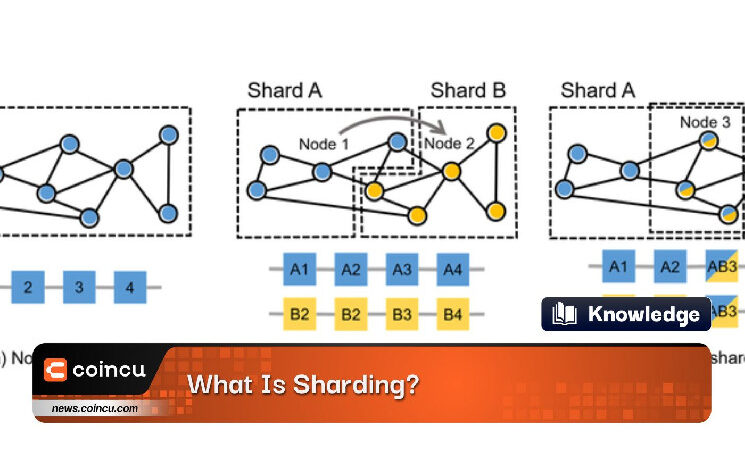
Sharding is a technique used in distributed database systems to improve performance, scalability, and availability. It involves dividing a large database into smaller, more manageable parts called shards. Each shard contains a subset of the data, and together, the shards form a complete database.
In a shared database, data is distributed across multiple servers or nodes. Each shard is responsible for storing and processing a portion of the data, and no single node contains the entire dataset. This allows for parallel processing and increased storage capacity, enabling the system to handle larger amounts of data and higher transaction rates.
The division of data into shards is typically based on a chosen shard key, which can be a specific attribute or a range of values. The shard key determines how the data is partitioned across the shards. By carefully selecting the shard key, the system can evenly distribute the data and balance the workload across the nodes.
Sharding offers several advantages:
- Scalability: As the amount of data grows, additional shards can be added to the system, allowing it to handle increased workloads and support more users without sacrificing performance.
- Performance: Sharding enables parallel processing by distributing data across multiple nodes. This can result in faster query response times and improved overall system performance.
- Availability: Since the data is distributed across multiple nodes, the failure of one node does not result in the complete unavailability of the system. The remaining nodes can continue to serve requests and maintain data availability.
However, sharding also introduces some challenges. Complex queries that require data from multiple shards can be more difficult to execute, and maintaining data consistency across shards can be challenging. Additionally, sharding requires careful planning and management to ensure proper distribution of data and load balancing.
Sharding is a powerful technique for scaling and improving the performance of distributed database systems, making them capable of handling large volumes of data and high workloads.
Understanding Sharding
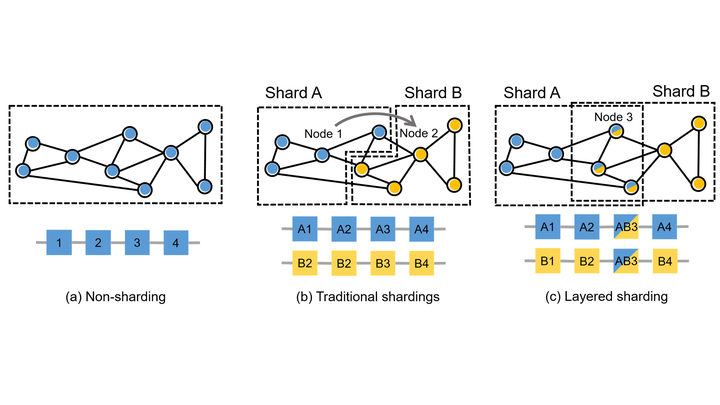
Sharding is a technique used in database systems to horizontally partition data across multiple servers or nodes. It involves breaking down a large database into smaller, more manageable pieces called shards. Each shard contains a subset of the data, and together, the shards form a complete database.
The primary goal of sharding is to improve the performance and scalability of a database system. By distributing data across multiple shards, the workload can be spread out, allowing for parallel processing and increasing the system’s capacity to handle larger volumes of data and higher transaction rates.
Here are some key aspects to understand about sharding:
- Data Distribution: Sharding involves dividing data based on a shard key. The shard key can be a specific attribute or a range of values. It determines how the data is partitioned across the shards. For example, in a social media application, the shard key could be the user ID, ensuring that all data related to a particular user is stored in the same shard.
- Shard Independence: Each shard operates independently and can be located on a separate server or node. This allows for parallel execution of queries and transactions on different shards simultaneously. It also provides fault isolation, so if one shard fails, the other shards can continue functioning.
- Query Routing: When a query is made to the database, a sharding middleware or coordinator determines which shard(s) need to be accessed based on the query’s shard key. The middleware then routes the query to the appropriate shard(s) for processing. This ensures that queries are directed only to the relevant shards, reducing the amount of data that needs to be processed.
- Data Consistency: Maintaining consistency across shards can be a challenge in sharded databases. Updates that affect multiple shards, known as distributed transactions, require coordination to ensure data integrity. Different approaches, such as two-phase commit or eventual consistency, can be used to manage consistency across shards.
- Shard Management: Sharding requires careful planning and ongoing management. The number of shards, their distribution, and the shard key selection impact the system’s performance and scalability. Scaling the system may involve adding more shards, redistributing data, or redefining the shard key.
- Shard Awareness: Applications that interact with a sharded database need to be shard-aware. They must be designed to route queries correctly, handle distributed transactions, and manage data locality. Proper application design and development practices are necessary to leverage the benefits of sharding effectively.
Sharding is commonly used in large-scale systems where traditional approaches to scaling a database, such as vertical scaling (adding more resources to a single server), become impractical or insufficient. It enables the system to handle massive amounts of data and heavy workloads while maintaining performance and availability.
How Sharding Is Accomplished
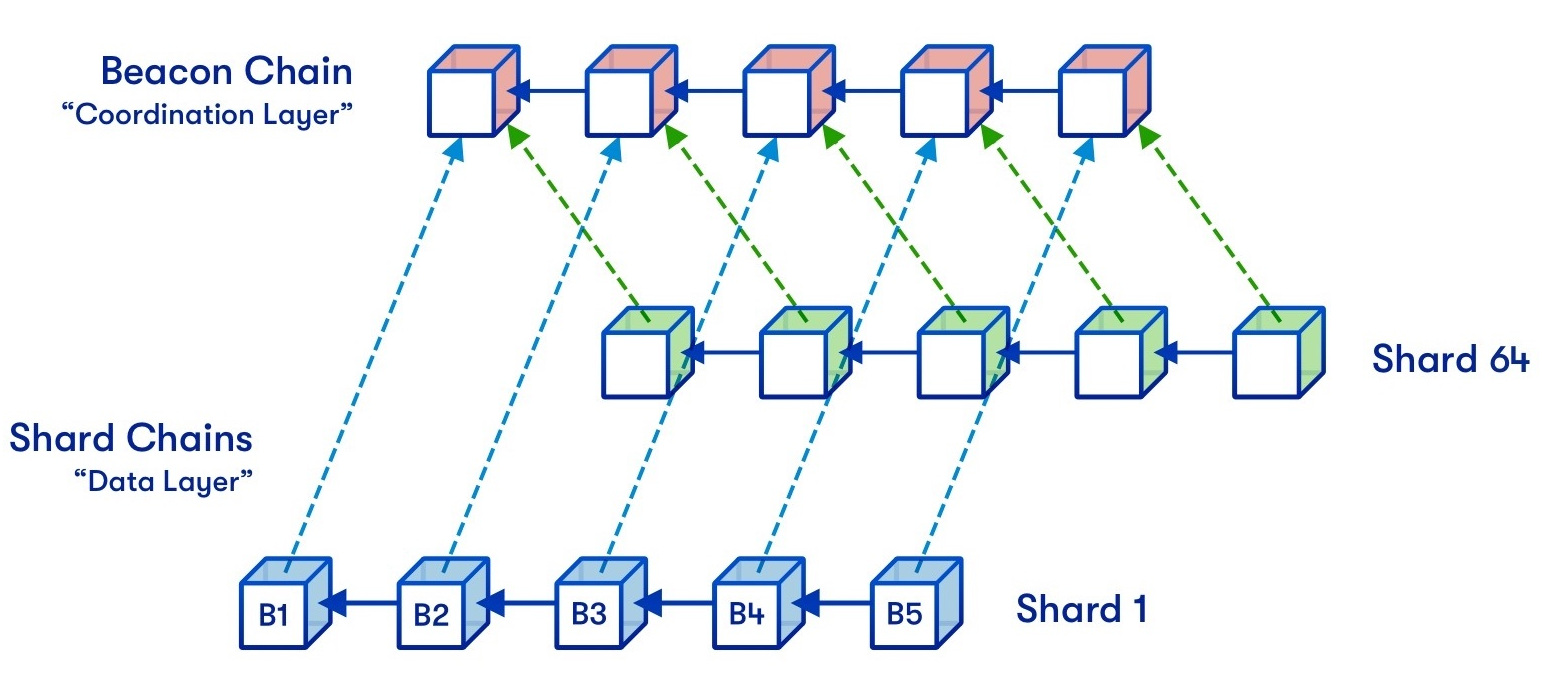
Sharding is accomplished through a combination of data partitioning, query routing, and shard management techniques. Here’s an overview of how sharding is typically accomplished:
- Data Partitioning: The first step in sharding is to divide the data into smaller subsets called shards. There are several common approaches to data partitioning:a. Range-based partitioning: Data is divided based on a specified range of values. For example, if the shard key is a timestamp, one shard may contain data for a specific time period (e.g., January 1 to January 31), while another shard contains data for the next time period (e.g., February 1 to February 28).b. Hash-based partitioning: Data is distributed across shards based on the hash value of the shard key. The hash function evenly distributes the data, ensuring a roughly equal distribution across shards.c. List-based partitioning: Data is partitioned based on a predefined list of values. Each shard is assigned a specific value or set of values for the shard key. For example, if the shard key is a country code, one shard may contain data for the USA, while another shard contains data for Canada.
- Query Routing: When a query is made to the database, a sharding middleware or coordinator is responsible for determining which shard(s) need to be accessed. This is done based on the query’s shard key. The middleware keeps track of the shard mappings and routes the query to the appropriate shard(s) for processing. The query results from multiple shards may be combined or aggregated before being returned to the user.
- Shard Management: Sharding requires ongoing management to ensure the proper distribution of data and load balancing. Some common tasks involved in shard management include:
a. Shard Creation: As the data grows, new shards may need to be created to accommodate the increased workload. This involves allocating new servers or nodes and redistributing the data across the existing and new shards.
b. Shard Removal: If the data size decreases or the workload decreases, it may be necessary to remove shards from the system. The data from the shard is redistributed to the remaining shards before the shard is decommissioned.
c. Data Redistribution: As the number of shards changes, data may need to be redistributed to maintain a balanced distribution across the shards. This process involves moving data between shards while minimizing downtime and maintaining data consistency.d. Shard Key Refinement: The choice of a shard key is crucial for efficient sharding. Over time, it may be necessary to review and refine the shard key selection to ensure an even distribution of data and optimal query performance.
Sharding requires careful planning and coordination to ensure data consistency, efficient query routing, and effective management of the shards. It is important to consider factors such as data distribution, query patterns, scalability requirements, and system complexity when implementing a sharding strategy.
Sharding and Security
Sharding can have implications for security in a database system. Here are some considerations regarding security when implementing sharding:
- Data Segmentation: Sharding involves dividing data into smaller subsets or shards. It’s important to carefully consider how data is segmented to ensure that sensitive or confidential information is appropriately protected. For example, you may want to avoid placing highly sensitive data in the same shard as less sensitive data to minimize the risk of unauthorized access.
- Access Control: Sharded databases need robust access control mechanisms to ensure that only authorized users or applications can access specific shards or data. Role-based access control (RBAC), fine-grained access control policies, and strong authentication mechanisms should be implemented to enforce access restrictions and protect sensitive data from unauthorized access.
- Encryption: Encrypting data at rest and in transit is essential to protect data confidentiality. Sharding should not compromise the use of encryption mechanisms. Each shard should have encryption implemented to safeguard data within the shard. Additionally, when data is transmitted between shards or during query routing, appropriate encryption protocols (such as TLS/SSL) should be used to prevent eavesdropping or tampering.
- Data Integrity: Maintaining data integrity across shards is crucial. Distributed transactions involving multiple shards should ensure that all data changes are either committed successfully across all relevant shards or rolled back in case of failure. This ensures that the integrity of the overall dataset is maintained and that no unauthorized modifications or inconsistencies are introduced.
- Audit and Logging: Sharded databases should have comprehensive logging and auditing mechanisms in place. This includes tracking and logging all significant operations, access attempts, and modifications made to the data. Centralized logging and monitoring can help detect any suspicious activities or security breaches across multiple shards.
- Network Security: Sharded databases typically involve multiple servers or nodes communicating with each other. It’s essential to secure the network communication between shards, ensuring that it is protected against unauthorized access, eavesdropping, or interception. Strong network security measures, such as firewalls, VPNs, and secure communication protocols, should be implemented to secure the inter-shard communication.
- Compliance and Regulations: Depending on the nature of the data being stored, specific industry regulations or compliance requirements (such as GDPR, HIPAA, or PCI DSS) may need to be considered. Sharding strategies should align with these regulations to ensure data privacy, protection, and compliance.
- Vulnerability Management: Regular security assessments, vulnerability scans, and penetration testing should be conducted on the sharded database system to identify and address any security vulnerabilities. Prompt patching of software and firmware vulnerabilities and following security best practices will help mitigate potential security risks.
Conclusion
Sharding is a technique used in distributed database systems to improve performance, scalability, and availability. It involves dividing a large database into smaller parts called shards, which are distributed across multiple servers or nodes. Each shard contains a subset of the data, enabling parallel processing and increased storage capacity.
Sharding offers several advantages, including scalability to handle larger data volumes and higher workloads, improved performance through parallel processing, and increased availability by distributing data across multiple nodes. However, sharding also presents challenges such as maintaining data consistency across shards and managing complex queries that involve multiple shards.
Security considerations are important when implementing sharding, including data segmentation, access control, encryption, data integrity, and compliance with regulations. Proper security measures, such as robust access controls, encryption, audit logging, and vulnerability management, should be implemented to protect data and ensure compliance with security standards.
Overall, sharding is a powerful technique for scaling and improving the performance of distributed database systems. It requires careful planning, effective management, and adherence to security best practices to fully leverage its benefits and ensure the security and integrity of the data.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.